Cyber Maturity Assessment
The ROCK Cyber Maturity Assessment is an integral component of a comprehensive cyber security strategy. Learn more about our Cyber Maturity Assessment below, or submit the form to book your free consultation.
Book Your Free Cyber Maturity Consultation Today
Speak with one of our cyber security specialists today and discover how the ROCK Cyber Maturity Assessment will benefit your organisation.
We’ve earned the trust of leading UK brands























Managing the evolving cyber security landscape can be a significant challenge...
Cyber security is a paramount concern for organisations of all sizes. The increasing frequency and sophistication of cyber threats necessitate a robust and mature cybersecurity posture.
To address this critical need, we created the ROCK Cyber Maturity Assessment.
ROCK will work with you to understand your current Cyber Security position and business needs. As your strategic partner, we can make a plan to measure – a perfect fit to help you mitigate the risk and reduce the burden on your internal IT team.
You can rest assured that the Cyber Security Assessment is based on the internationally recognised Critical Security Controls (CSC) v8 framework, published by the Center for Internet Security (CIS).
You can also give us a call on 0770 010 1864
or send us an email at hello@rock.co.uk

Understanding your cyber maturity score
The ROCK Cyber Maturity Assessment uses a zero-trust security architectural approach that analyses all security risks facing your organisation based on data from the company infrastructure, e.g. endpoints, Active Directory, Microsoft 365 and Azure. This ranges from data security and compliance, to endpoint management. All elements are scored using the standardised scoring system below. We then provide our expert recommendations for each.
Level 1: Basic
The security attention is on the tactical level. The risks of a cybersecurity issue are severe.
Level 2: Standardised
The security attention is on the proactive level. The risks of a cybersecurity issue are significant.
Level 3: Rationalised
The security attention is on the holistic level. The risks of a cybersecurity issue are moderate.
Level 4: Dynamic
The security attention is on the strategic level. The risks of a cybersecurity issue are minor.
How we use the cyber maturity score to understand your systems
Our cyber maturity assessment provides a detailed and comprehensive analysis of your organisation’s current cybersecurity maturity, identifying strengths and vulnerabilities.
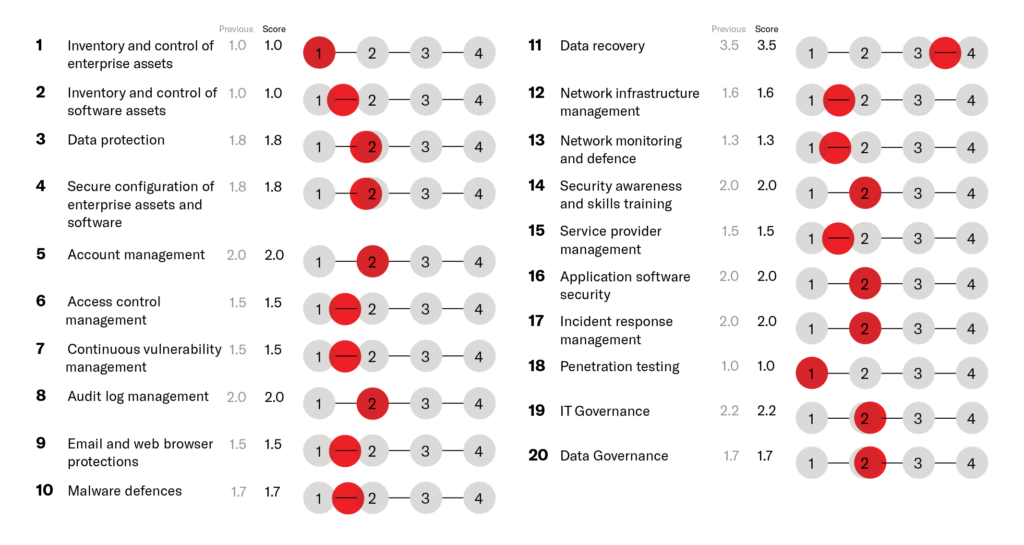
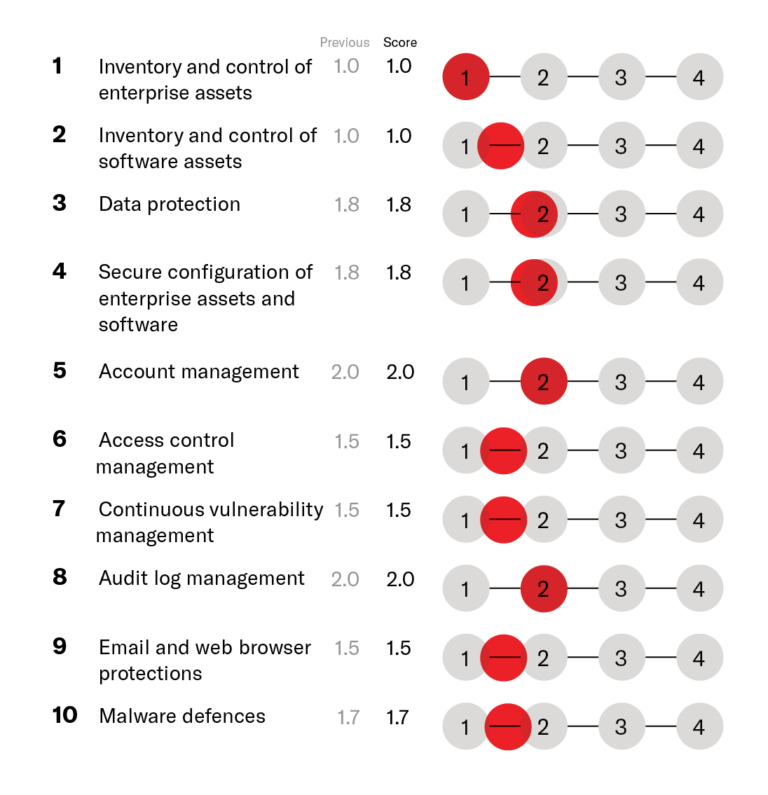
We deliver practical, specific recommendations to mitigate identified risks, ensuring your organisation can take immediate steps to improve its cybersecurity stance.
Whether you’re a business looking for an established Cyber Security partner, or an IT Manager with an in-house team looking to extend your capabilities, ROCK can help you get where you need to go.
Say goodbye to your IT security burdens and let us craft a rock-solid Cyber Security plan that your stakeholders and communities can truly rely on.
ROCK will work with you on a detailed plan of approach

“I always recommend that companies take advantage of our cyber maturity assessment. Without conducting this full review, organisations remain at risk of increasing Cyber threats.”
Tom Aubin, Director of Consulting
The below plan of approach is our suggestions to prioritise the recommendations. The priority takes into account the urgency, estimated effort and complexity.
Recommendations: 0-30 days
We recommend in the 0-30 days to focus on the so-called ‘low-hanging fruit’ features (features that are relatively easy to implement, yet with high impact on preventing security incidents).
Examples:
• Delete old and unused computer accounts from the Active Directory
• Disable old and unused accounts in all applications
• Create a process to ensure that all applications are kept to up to date
Recommendations: 30-90 days
The 30-90 days focuses on features that further harden your IT environment, and on implementing governance and reporting features.
Examples:
• Create a process to regularly review external users
• Implement tooling to ensure all emails are scanned for malware, phishing, and spam
• Ensure all external (web)services are protected against DDoS attacks
Recommendations: 90+ days
Finally, the 90+ days items covers the creation/revision of processes, and implementation of solutions that take a longer preparation time.
Examples:
• Implement Microsoft 365 and Azure governance features and automated reports
• Deploy the hardening baseline to all the organisation’s devices (mobile included). This to reduce the attack surface of all the organisation’s devices. Ensure the baselines are updated every six months
• Validate backups by regularly exercise the disaster and recovery procedures
Top advised software and estimated investment
We highlight the top advised software to ensure your organisation is building and maintaining a mature security posture.
We then provide an overview of your estimated investment, benchmarked against industry standards to ensure you are paying the optimal amount.
Why choose ROCK for your cyber maturity?
Comprehensive Understanding of Cybersecurity Posture
Our cyber maturity assessment provides a detailed and comprehensive analysis of your organisation's current cybersecurity maturity, identifying strengths and vulnerabilities.

We recommend industry-leading Microsoft solutions, including Microsoft 365, Microsoft Azure, Microsoft Copilot, Microsoft Intune, Defender for Cloud Apps, and Defender for Endpoint, as key components of a robust cybersecurity strategy.
Actionable Recommendations
We deliver practical, specific recommendations to mitigate identified risks, ensuring your organisation can take immediate steps to improve its cybersecurity stance.
Strategic and Practical Guidance
Our strategic recommendations and step-by-step plans are segmented into 0-30, 30-90, and 90+ day phases, providing a clear roadmap for your cybersecurity improvements.
Framework-Based Approach
Our methodology is rooted in the internationally recognised Critical Security Controls (CSC) v8 framework by the Centre for Internet Security (CIS), ensuring a structured and effective approach to cybersecurity.
Investment and Cost Efficiency
We offer an overview of the investment required and a cost comparison to industry standards, helping clients budget effectively while achieving significant cybersecurity enhancements.
Interested in understanding how we can improve your Cyber Maturity?
Interested in understanding how we can improve your Cyber Maturity?
If you would like to speak to us about your Cyber Security requirements, please complete this form and schedule time with one of our dedicated specialists at a time that works for you.

Book Your Free Cyber Maturity Consultation Today
Speak with one of our cyber security specialists today and discover how the ROCK Cyber Maturity Assessment will benefit your organisation.