As the market for hacking tools and capabilities expands, cyber attackers are becoming more skilled than ever.
With the growing commercial availability of cyber intrusion software, concerns surrounding cybersecurity measures, risks, and infrastructure vulnerabilities are rising. That’s why addressing the vulnerabilities in your systems is more important than ever.
What can you do to protect yourself from this risk? Read on to learn how Vulnerability Assessments work and how ROCK’s Vulnerability Assessment Service can benefit you.
What is a cyber vulnerability?
A cyber vulnerability is a weakness that exposes you to cyber-attacks and associated risks such as data loss, operational disruption, and reputational damage (to name a few).
There are varying degrees of vulnerabilities, each posing varying degrees of risk. Whether you run a traditional on-premise infrastructure, in the Cloud, or hybrid, Cybercriminals can exploit these vulnerabilities.
As such, any organisation can be vulnerable to cyber-attacks. The consequences of these attacks range from compliance violations and supply chain disruption to intellectual property theft and severe financial loss.
What is a Vulnerability Assessment and how do they work?
A vulnerability assessment, also known as a vulnerability analysis or test, reveals the weaknesses and entry points in your infrastructure which attackers target to infiltrate your organisation. In other words, they provide you visibility of your environment’s weak points.
At ROCK, we know that the threat of cyber threats can be worrying. Leveraging the information on current and possible entry points, we will help you identify your weaknesses and will work with you to create an improvement plan.
During vulnerability testing, an engineer will install a scanning agent on each device within your network. The agent will collect information on your environment to log and highlight any current and potential security risks.
At ROCK, we provide our clients with a detailed assessment report after assessing their vulnerabilities, ranking them by risk level for easy understanding. We will assign a vulnerability score to the risks, taking into account their likelihood and potential impact.
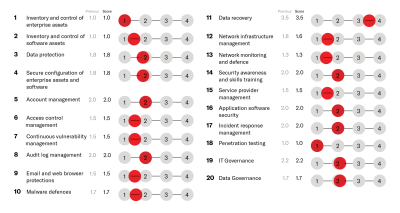
Not all vulnerabilities carry the same level of risk; weak passwords and website vulnerabilities present differing degrees of threat. ROCK will help you determine which risks to prioritise by indicating their likelihood and potential impact on you.
Our vulnerability reports will show you the likelihood of each risk occurring whilst the potential consequences of each risk. The dedicated engineer will record potential risks in a risk register, reviewing them at key points during new or ongoing projects for overall vulnerability management.
We will work with you to create a forward-looking roadmap, ensuring continuous evolution and strengthening of their cybersecurity posture. We will provide you with a list of important suggestions with estimated costs. This will help your organisation understand the amount of money involved in managing the identified and possible risks.
If this is even a consideration, book a free 30-minute consultation with our experts to discover how a vulnerability assessment with ROCK can benefit you.
Vulnerability Assessments vs Penetration Tests
Vulnerability Assessments and Penetration tests are often confused with each other. Although similar, their processes produce different results.
Vulnerability assessments involve using network scanning tools to identify known and potential vulnerabilities. However, penetration tests actively attempt to breach a system through simulated cyber-attacks to evaluate the security of the infrastructure.
Why is this distinction important? Both vulnerability assessments and penetration tests work together to evaluate an organisation's security posture. They’re often used alongside each other to assess an organisation’s vulnerabilities and protection processes.
Types of Vulnerability Assessments: Baseline and Ongoing
ROCK conducts two types of vulnerability assessments throughout our client’s lifecycle in our care: Baseline and Ongoing.
Baseline assessments are conducted as an initial evaluation of the infrastructure to identify vulnerabilities. We compare the results against industry security benchmarks, establishing a starting point for your security improvement plan.
Ongoing assessments are part of a continuous process which follows the initial baseline assessment, typically taking place monthly.
Together, these assessments continuously monitor and adapt our clients to emerging threats or changes alongside introducing new measures.

What are the most common vulnerabilities?
The most common vulnerabilities, in no particular order, are:
Inactive/dormant accounts or computers
Inactive computers miss security updates and patches, serving as entry points for cybercriminals. Attackers may target dormant accounts, exploiting weak passwords or other associated vulnerabilities.
Unsupported operating systems or applications
Unsupported (end-of-life) systems and applications pose risks as they lack necessary security updates, increasing susceptibility to malware, data breaches, and system compromises.
Password problems
Weak passwords (e.g., simple, easily guessable ones) are at risk as they are susceptible to brute-force attacks. Stolen passwords from data breaches often appear on the dark web. If employees reuse these compromised passwords, attackers can gain unauthorised access to corporate accounts.
User behaviour
Poor security practices (e.g., sharing credentials, and clicking on phishing links) can lead to breaches. Not enabling automatic screen locks also poses a security risk as unattended devices can be accessed by unauthorised individuals, compromising sensitive information.
Unpatched software and systems
Neglecting updates for third-party applications (e.g., browsers, plugins) exposes organisations to attackers who exploit this vulnerability. Not applying security patches also leaves systems vulnerable to known exploits as attackers can target unpatched vulnerabilities.
You may be surprised by the simplicity of these common vulnerabilities. Weak passwords, outdated software, and unattended devices may seem like basic issues. However, they’re exactly why understanding your organisation’s weak points is crucial.
These seemingly ‘basic’ weak points can often go overlooked when their impact is not assessed. ROCK’s experts take the guesswork out of uncovering your vulnerabilities. We help you identify possible and current risks before it’s too late.
Does my business need a Vulnerability Assessment?
- Does your organisation rely on critical systems and networks to drive its operations?
- Do you store sensitive information about clients and internal employees?
- Does your organisation use the Cloud, an on-premise server, or a hybrid of both?
If any of these concerns you, a Vulnerability Assessment will prove beneficial for your security posture.
Ready to secure your organisation? Book a free 30-minute consultation with our experts to discover how a vulnerability assessment with ROCK can benefit you. Protect your data, prevent breaches, and stay ahead of cyber threats.